Configuring FTP Server Software To Operate Behind an SMC Barricade V1.2
In the most basic configuration you can simply redirect TCP port 21 to the FTP server and Active mode FTP transfers will work however PASV will not.
Active mode FTP works because when the client sends the request to the server it issues a PORT command to the server which tells it the IP address and port which it is listening on. The FTP server then initiates a connection to the client.
PASV mode FTP does not work because the client issues the PASV command and the server responds with itís IP address and port it is listening on and it is the client that makes the connection to the server on this port. There are two problems associated with this:-
- The server gives itís own IP address in the response. If the server is behind a NAT firewall such as a SMC Barricade then this IP address is a private one such as 192.168.123.1 and is not contactable from the Internet.
- Normally the FTP server may listen on any port above 1023 for PASV connections and this raises security concerns if you enable all these ports to forward to your FTP server. Many of the ports you will be allowing are normally used by Back Orifice and other trojansÖ
SMC PASV Bug
Some SMC Barricade routers (specifically the 7004BR) have a bug/feature where an incoming PASV command is converted to P@SW and rejected by the FTP server. The intention of this feature was to make the client think that the server does not support the PASV mode and resort back to using active mode instead. In reality virtually no ftp client software will do this so all this feature accomplishes is to stop FTP server software from working even if it does have the features to support PASV from behind a firewall.
Configuration Required for Active FTP to Work
All you need to do is enable port 21 to be forwarded to your FTP server. This is done in the Ďvirtual serversí page.
Clients behind a firewall may not be able to connect. This is because the client issues a PORT command providing itís IP address and port that it is listening on. The firewall may be configured not to let the FTP server talk back to the client. In addition if the firewall also used NAT (Network Address Translation) the client will be telling the server completely the wrong IP address!
Note that the SMC Barricade is the more intelligent type of firewall and will look at the commands being issued by the client behind the SMC to the FTP server somewhere on the Internet and automatically modify the IP address etcÖ in the PORT command to itís IP address and permit back the connect from the FTP server.
This is the reason for the Ďnon standard FTP portí section of the SMC configuration. If the FTP server is not running on port 21 then the SMC would not know that it should be looking out for PORT commands from the client!
Testing the FTP server is a little problematic. If you connect to the private IP address (192.168.123.1 for example) then it should work fine. However if you connect using the public IP address (the IP address all the users on the Internet would use) then you will find that it stops working on the first data connection (typically a directory listing). What you would expect to happen is:-
- Client issues PORT command to server.
- SMC translates PORT parameters to itís IP address and a chosen port.
- Server connects to supplied IP address and port by SMC.
- SMC redirects the data to the original IP address and port originally specified by the client.
It is stage (4) that goes wrong. The SMC is expecting this data to come in via the WAN (Internet connected) port and simply ignores the data when it comes in from the LAN side. This results in the data connection timing out.
In reality this does not cause a problem. Clients on the Internet can connect via active FTP without problems. If you want to connect yourself just use the private IP address instead.
Configuration Required for Passive (PASV) Mode to Work
For Passive mode to work you have to do four things:-
- Tell the FTP server software the external IP address of the SMC so that it advertises that IP address instead .
- Configure the FTP server software to use a specific limited range of ports for PASV mode.
- Configure the SMC Barricade to forward these PASV ports to the FTP server.
- Overcome the P@SW bug if present in your SMC Barricade.
Not all server software will support features (1) and (2) above and only a very few will support (4).
Serv-U (Windows)
Serv-U has the required features except for (4) to overcome the P@SW bug. Unfortunately you donít tend to get source code for Windows programs so you cannot modify the software yourself to get it to work. I am not aware of any Windows programs which will get around this bug.
Step 1 Ė Configuring the servers real IP address
The graphic below shows where you configure the external IP address of the FTP server.
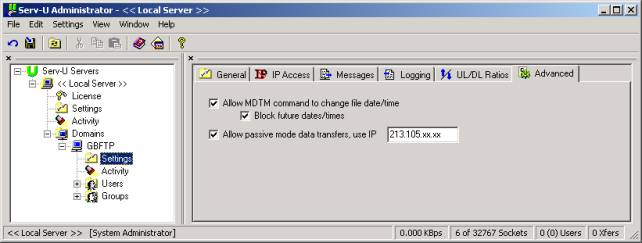
Step 2 Ė Configuring the PASV port range
The graphic below shows you where you configure the PASV port range to use. As a general rule you should allocate enough ports to support the number of simultaneous connections you will allow.
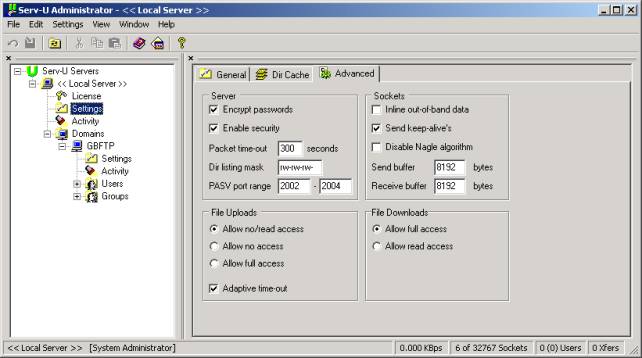
Step 3 Ė Reconfiguring port forwarding
The last step is to reconfigure the port forwarding so that as well as port 21 the ports specified for the PASV range are also forwarded to your FTP server.
RaidenFTPD (Windows)
I have recently been contacted by RaidenFTPD team who let me know that they now support the P@SW command which the SMC Barricade produces. Therefore this would probably be the best windows ftp server to use. I haven't tried it myself though as I no longer have a Barricade router.
For more information see http://www.raidenftpd.com/kb/kb000000015.html and http://www.raidenftpd.com/en/
Pure-ftpd (Unix)
This is the FTP server software that I run. It is designed to be secure but itís configuration is all parameters to the daemon when it starts and there is no configuration file. However it has many usefull features and is constantly being developed.
I modified the source code so that the server treats the PSW and the PASV command as being identical. This patch has been included into the main package as from version 1.0.4 so if you install any version from 1.0.4 it will work fine with any SMC Barricade. You can download the software from:-
http://pureftpd.sourceforge.net/
Shown below is a section from my /etc/rc.d/init.d/pure-ftpd file showing the parameters I use :-
start() {
echo -n $"Starting pure-ftp services: "
# -c 3 = max 3 simultaneous connections
# -C 2 = max 2 from same IP
# -E†† = no anonymous logins
# -I 1 = 1 min idle timeout
# -j†† = auto create home dir
# -O†† = stats log file
# -p†† = PASV port range
# -P†† = PASV IP
# -T†† = upload/download bandwidth
# -l†† = User account search
††/usr/local/sbin/pure-ftpd -c 3 -C 2 -E -I 1 -j -O stats:/var/log/pure-ftpd -p 20000:20005 -P 213.105.x.x -T 12:32 -l puredb:/etc/pureftpd.pdb -l unix &
RETVAL=$?
echo
[ $RETVAL -eq 0 ] && touch /var/lock/subsys/pure-ftpd
status pure-ftpd
return $RETVAL
}
So Whatís Port 20 Used For?
Port 20 is used in active FTP data connections and is the port the FTP server initiates the connection from. Since the SMC permits all outbound connections you donít have to permit port 20 outbound (there is no section to configure it in).
If you had a firewall which you could restrict the outgoing connections such as a Cisco router then you could make use of this feature. If you have a Cisco router which was configured to permit only particular data from going out on the Internet you would need to add something like the following to the outbound access list:-
ip access-list [name-or-number] permit tcp host [ftp-server] eq 20 any gt 1023